About MAC Address Generator The online MAC Address Generator is used to generate a random MAC address, in lower or upper case for your convenience. The tool can generate four most commonly used types of MAC address formats and it is also allowed to specify your preferred MAC address prefix (specific OUI - Organizationally Unique Identifier). Please note that the generated MAC addresses are for testing purpose only, not for production use. MAC address MAC address (Media Access Control address) is a unique identifier assigned to network interfaces for communications on the physical network segment. It usually encodes the manufacturer's registered identification number. If you want to find the manufacturer a certain MAC address belongs to, please use our tool.
Free mmo games for kids. The first question you might have about this instructable is why would I need to spoof my MAC address. Well, there are two answers. One, you need to change your MAC address so you network will recognize your device and allow it to connect. Two, for malicious purposes you may need to spoof you MAC address so you could gain access to networks or to hide who you really are. Spoofing your MAC address is legal and can be done safely within Windows without any external software.
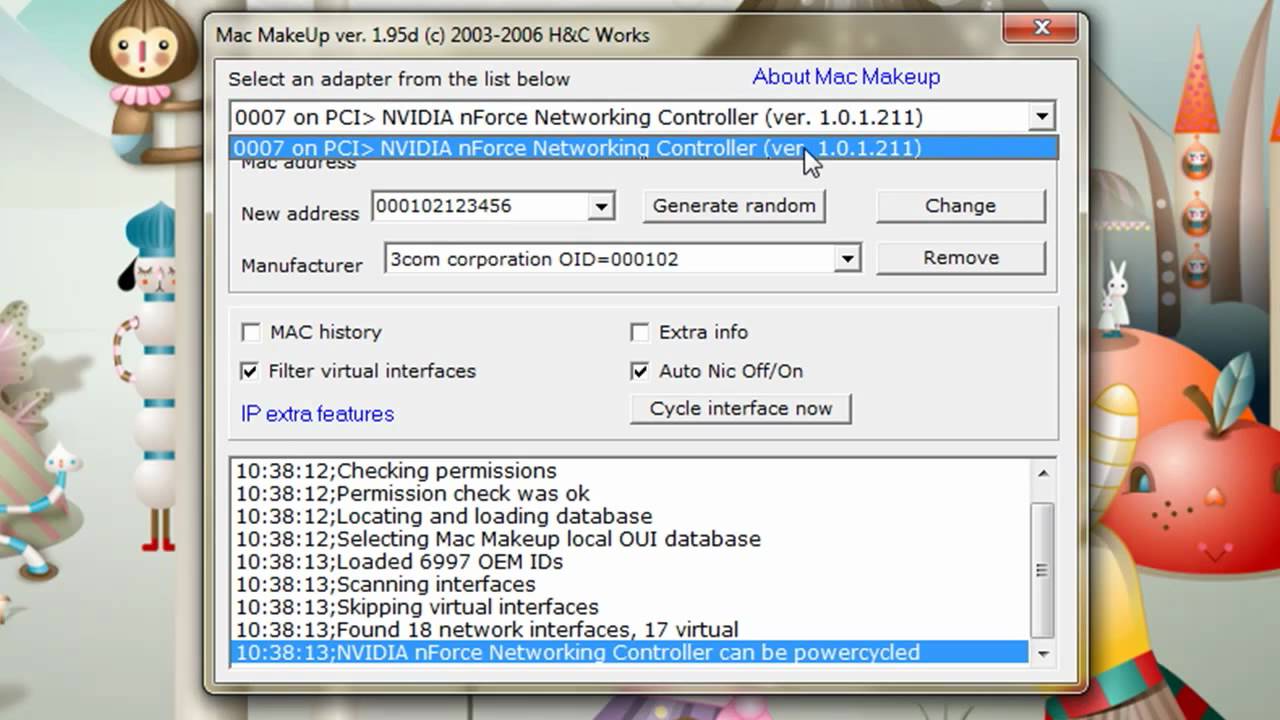
The first step in spoofing your MAC address is to find the network interface device that you want to spoof. Go to Start>Control Panel>Network Connection. Then double click on the device that you want to spoof. Then click on the support tab and then click on details. Then in the list you will see the MAC address.
If you use this to spoof you MAC address for Malicious purposes I cannot be held responsible. Jason, CEO/Lead Engineer JNETechnologies. FMR--USAF Special Operations Command at A.F. Information Warfare Center FL, NV. Simply put, I assign a =. Well about this theme is very cool to bring it on. Do you know that Mac Spoofing is not illegal.??????
Well yes give a check out. So the question is if Mac Addresses is a layer 2 operation that occurs inside your network.What the hell I will do with that? I use a laptop with 'Kali' installed in it.
In places that I want to see if the Wireless is secure I connect with and use the software aircrack to obtain info of the Access Point on the Place. And then I copy one of this mac address to my wifi card and connect it to the Network. And I gain access in no time. The only way to avoid this is using MAC Filtering if the router has the capability activated. Well you will be surprised that the process of accessing a web server lets say Google. They do not have neither your router mac address, neither your device mac address, and neither your private ip addressing.
Yes they have your provider name using the ip addressing that is unique and public. Let me give you a flash example of me using Netflix you can try this at home like educational purposes. I fly to from Mexico to Philadelphia.
Focus inbox outlook for mac. When I access Netflix because of the IP Addressing they gave me the menu of USA Netflix. I was checking for 'La Reina del Paraiso' so was not there.
I went to google and I search for 'proxy server list for free' so one of Mexico appears. I put that in my browser. And also do a test using what is my ip site. For Netflix I am in mexico with the changes I did on the browser connection. So I access my favorite series of Mexico.
So try this with different places you will see how cool it is. Readers, know that even each PC, TV, PDA.is produced using a vast number of comprising pieces of hardware, each having it's own unique MacID. This makes conclusive ID even easier and without doubt. Do the math If x=number of MacID's within a, say, laptop, a low end would be x=(x)x2. Figure 100 ID's internally. Now x=100x100x100.
So, 0=100,000,000. Now, account for appx. 350(x), an iPad. To cam., to, touch sense, to, Bluetooth adaptor.
That is the ONLY device on earth containing these exact groupings of device MacID's. Tweek at least PC MacID. Proceed to create say 40 VM's on your VWAN. Tweek Location Services, PC Time and map out 38 hops in route. The more Mac's you tweek the better.
DO NOT MESS WITH THE TIER 5 GOV AGENCIES!!! We introduced MIPEM before creating algorithms to deal with this paradox of variables with regards to Trace Identification Protocol. Read beloy and then again below.